Virtualization and containers are transformative technologies that have significantly altered the landscape of IT infrastructure, offering enhanced flexibility, scalability, and efficiency. These technologies enable organizations to optimize resource usage, simplify management, and deploy applications more rapidly. This article explores the concepts of virtualization and containers, their benefits, and how they contribute to modern IT environments.
Virtualization
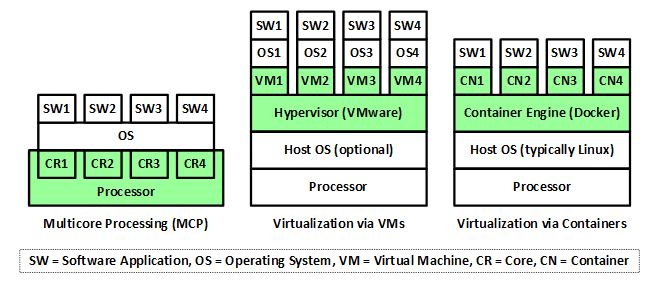
Virtualization involves creating virtual instances of physical hardware, enabling multiple virtual machines (VMs) to run on a single physical server. Each VM operates independently with its own operating system, applications, and resources, as though it were a separate physical machine.
Benefits of Virtualization:
- Resource Optimization: Virtualization allows for efficient use of physical hardware by consolidating multiple VMs on a single server, reducing hardware costs and improving resource utilization.
- Scalability and Flexibility: Virtual machines can be quickly provisioned, scaled, or decommissioned based on demand, providing flexibility to adapt to changing workloads and requirements.
- Isolation: Virtual machines are isolated from one another, which enhances security by preventing issues in one VM from affecting others.
- Simplified Management: Virtualization tools and platforms, such as VMware and Hyper-V, provide centralized management of VMs, making it easier to monitor, configure, and maintain virtual environments.
- Disaster Recovery: Virtualization supports efficient backup and disaster recovery solutions by allowing entire VMs to be replicated and restored from backups.
How Virtualization Works:
Virtualization relies on a hypervisor, which is software or firmware that sits between the hardware and the VMs. There are two types of hypervisors:
- Type 1 Hypervisor (Bare-Metal): Installed directly on the physical hardware, it provides high performance and efficiency. Examples include VMware ESXi and Microsoft Hyper-V.
- Type 2 Hypervisor (Hosted): Runs on top of a host operating system, offering flexibility but with slightly reduced performance. Examples include VMware Workstation and Oracle VirtualBox.
Containers
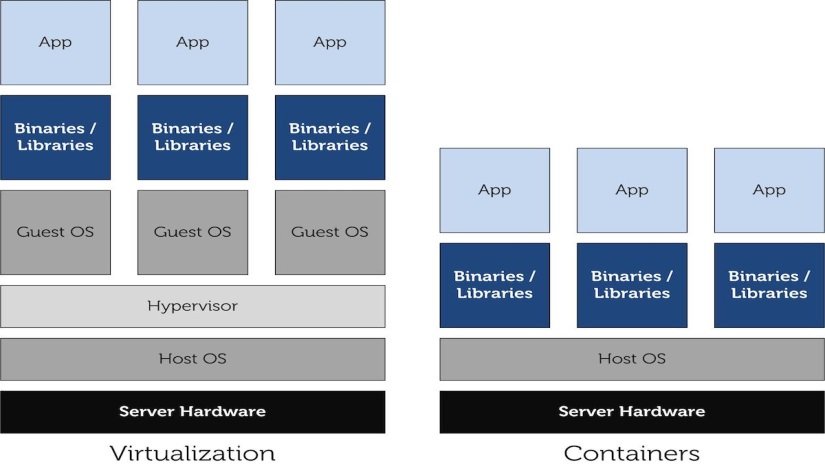
Containers are a form of virtualization that packages applications and their dependencies into a single, lightweight unit. Unlike traditional VMs, containers share the host operating system’s kernel but operate in isolated environments. This approach streamlines application deployment and management.
Benefits of Containers:
- Portability: Containers encapsulate an application and its dependencies, allowing it to run consistently across different environments, from development to production, regardless of the underlying infrastructure.
- Efficiency: Containers are more lightweight than VMs because they share the host operating system’s kernel, resulting in faster startup times and lower resource overhead.
- Scalability: Containers can be easily scaled up or down, facilitating dynamic and responsive application deployments. Container orchestration tools, like Kubernetes, automate scaling and management.
- Consistency: By packaging all necessary components together, containers ensure that applications behave the same way in different environments, reducing “works on my machine” issues.
- Isolation: Containers provide process and file system isolation, enhancing security by isolating applications from each other and from the host system.
How Containers Work:
Containers rely on container engines, such as Docker, to manage and execute containerized applications. The container engine uses container images, which are read-only templates that contain the application and its dependencies. Containers are instantiated from these images and run as isolated processes on the host operating system.
Virtualization vs. Containers
While both virtualization and containers offer isolation and resource optimization, they differ in their approaches:
- Virtualization: Provides complete isolation by running separate operating systems on virtual machines, which can be beneficial for running different OS types or applications with varied requirements. However, it incurs higher overhead due to the need for separate OS instances.
- Containers: Offer lightweight isolation by sharing the host OS kernel, making them ideal for deploying and managing microservices and applications in a more resource-efficient manner. Containers are more suitable for scenarios requiring rapid scaling and deployment.
Use Cases
- Virtualization: Often used in data centers for consolidating servers, running legacy applications, and providing isolated environments for testing and development.
- Containers: Commonly used in DevOps and CI/CD pipelines for consistent application deployment, microservices architectures, and cloud-native applications.
Conclusion
Virtualization and containers are powerful technologies that enhance IT infrastructure by offering flexibility, efficiency, and scalability. Virtualization provides robust isolation and resource optimization through virtual machines, while containers streamline application deployment and management with lightweight, portable units. By leveraging these technologies, organizations can achieve greater operational efficiency, reduced costs, and improved agility in their IT environments.