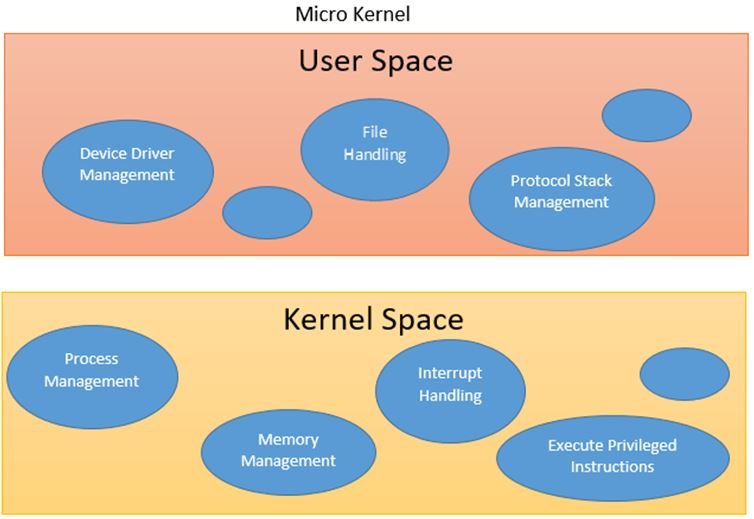
Virtualization technologies continue to revolutionize the landscape of operating systems (OS) in 2024, driving significant changes in how systems are managed, deployed, and scaled. This blog post explores the latest trends in virtualization technologies and their impact on modern operating systems, highlighting the advancements that are shaping the future of computing.
1. Advancements in Virtualization Technology
**1.1. Containerization
- Lightweight Virtualization: Containerization has become a key trend in 2024, offering a lightweight alternative to traditional virtual machines. Containers allow applications to run in isolated environments with minimal overhead, enhancing deployment speed and scalability.
- Kubernetes Integration: The use of Kubernetes for container orchestration has become more prevalent, providing robust tools for managing containerized applications across various environments. This integration simplifies deployment, scaling, and management of containerized workloads.
**1.2. Serverless Computing
- Event-Driven Architecture: Serverless computing, also known as Function as a Service (FaaS), is gaining traction. This model allows developers to write code that runs in response to events without managing server infrastructure. OSes are adapting to support serverless architectures, which enable more efficient resource usage and reduce operational complexity.
- Cost Efficiency: Serverless computing offers cost efficiency by charging only for the actual compute resources used during execution, eliminating the need to provision and manage servers.
2. Enhanced Virtualization Features
**2.1. Nested Virtualization
- Layered Virtualization: Nested virtualization allows virtualization to occur within virtual machines (VMs), enabling better isolation and management of nested environments. This feature is particularly useful for testing and development scenarios, where multiple layers of virtualization are required.
- Improved Performance: Advances in nested virtualization have led to improved performance and reduced overhead, making it a viable option for complex virtual environments.
**2.2. Hyperconvergence
- Integrated Infrastructure: Hyperconverged infrastructure (HCI) integrates compute, storage, and networking into a single, unified system. OSes are increasingly supporting HCI solutions, which simplify infrastructure management and enhance scalability.
- Simplified Management: HCI solutions offer centralized management interfaces and automation features, reducing the complexity of managing virtualized environments.
3. Impact on OS Deployment and Management
**3.1. Dynamic Resource Allocation
- Efficient Utilization: Virtualization technologies enable dynamic resource allocation, allowing OSes to allocate resources such as CPU, memory, and storage based on workload demands. This ensures efficient utilization of resources and enhances overall system performance.
- Automated Scaling: OSes are incorporating automated scaling features that adjust resources in real-time based on usage patterns, improving responsiveness and efficiency.

**3.2. Improved Disaster Recovery
- Snapshot and Cloning: Virtualization technologies provide snapshot and cloning capabilities that facilitate rapid recovery in case of system failures. OSes can leverage these features to create backup copies and restore systems quickly, minimizing downtime and data loss.
- Disaster Recovery as a Service (DRaaS): DRaaS solutions are gaining popularity, offering cloud-based disaster recovery options. OSes are integrating with DRaaS platforms to provide seamless recovery and business continuity.
4. Virtualization in Cloud Environments
**4.1. Cloud-Native Solutions
- Seamless Integration: Virtualization technologies are integral to cloud-native solutions, enabling the deployment and management of cloud-based applications. OSes are evolving to support cloud-native features, such as microservices and distributed architectures.
- Multi-Cloud and Hybrid Cloud Support: OSes are enhancing support for multi-cloud and hybrid cloud environments, allowing organizations to seamlessly manage and migrate workloads across different cloud platforms.
**4.2. Resource Optimization
- Cost Management: Virtualization technologies help optimize resource usage in cloud environments, reducing costs associated with underutilized resources. OSes are incorporating features to monitor and manage cloud resource consumption effectively.
- Performance Tuning: Advanced virtualization techniques enable performance tuning in cloud environments, ensuring that applications run efficiently and meet performance requirements.
5. Security Implications of Virtualization
**5.1. Isolation and Segmentation
- Enhanced Security: Virtualization technologies provide improved isolation and segmentation, reducing the risk of security breaches. OSes leverage virtualization to create secure environments for running sensitive applications and data.
- Micro-Segmentation: Micro-segmentation techniques allow for granular security policies within virtualized environments, enhancing protection against lateral movement of threats.
**5.2. Compliance and Governance
- Regulatory Compliance: Virtualization technologies support compliance with regulatory requirements by providing better control over data access and management. OSes are integrating features to facilitate compliance with industry standards and regulations.
- Governance Tools: OSes are incorporating governance tools to manage and monitor virtualized environments, ensuring adherence to policies and best practices.
Conclusion
Virtualization technologies are fundamentally reshaping operating systems in 2024, offering advancements that enhance efficiency, scalability, and security. From containerization and serverless computing to hyperconvergence and cloud integration, these technologies are driving innovation and transforming how systems are managed and deployed. As virtualization continues to evolve, operating systems will play a crucial role in leveraging these advancements to create more dynamic and resilient computing environments.