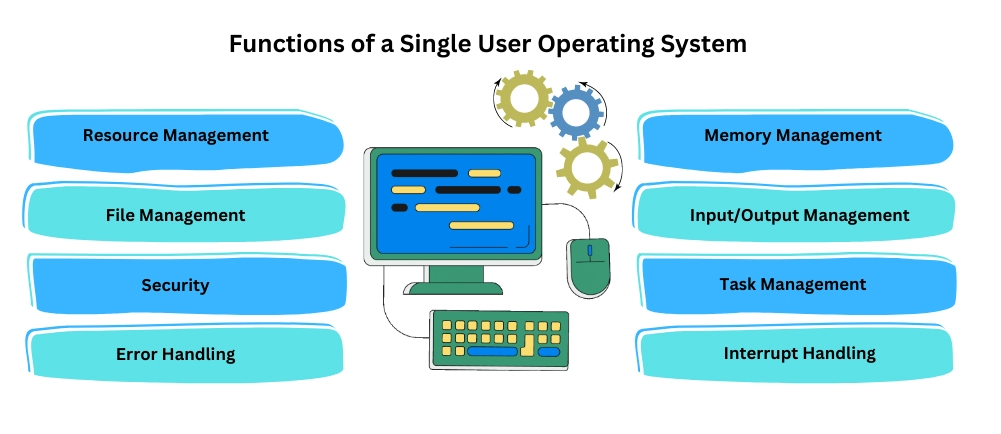
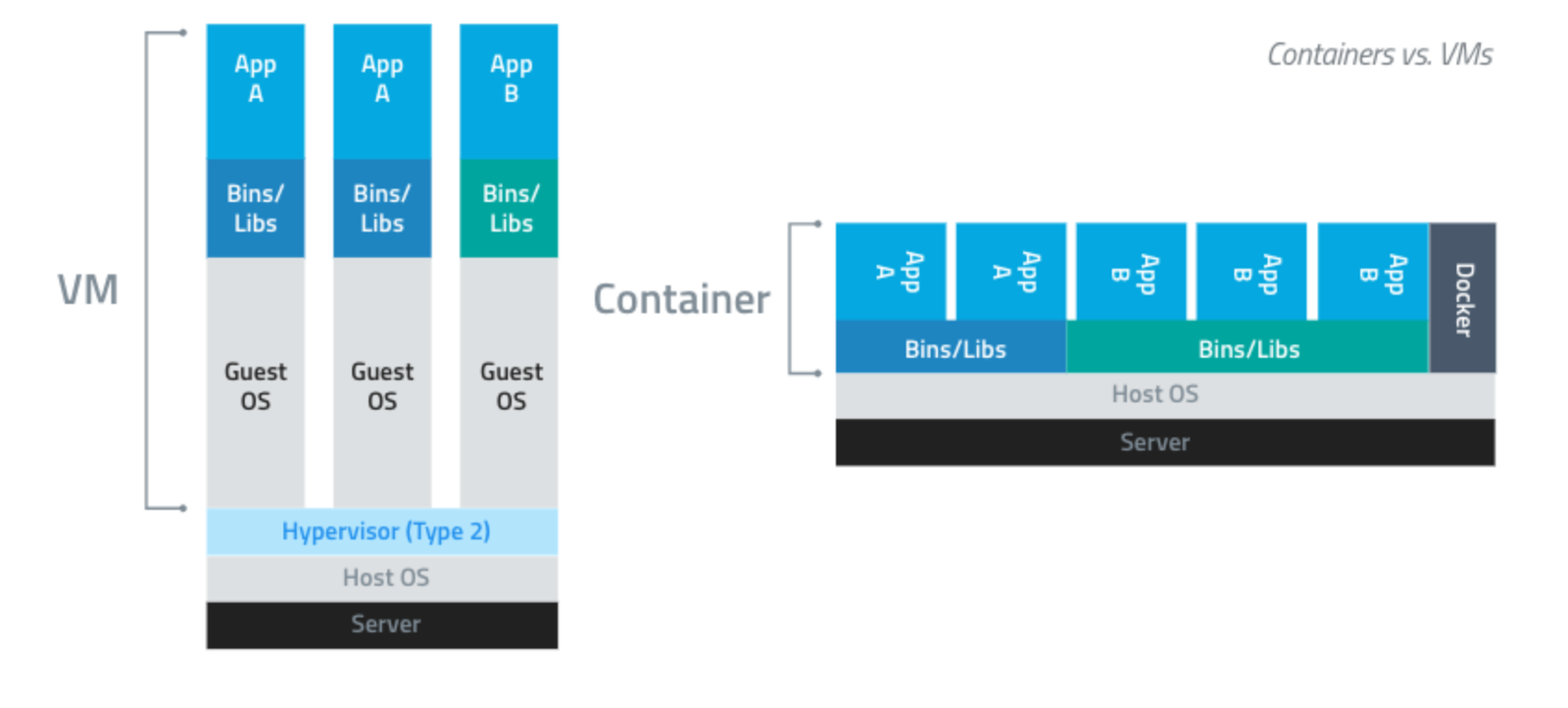
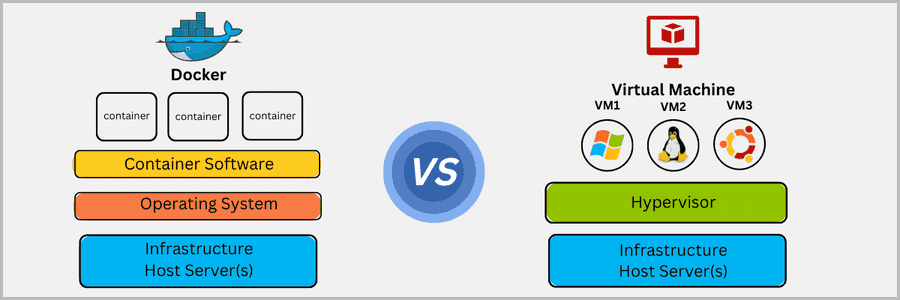
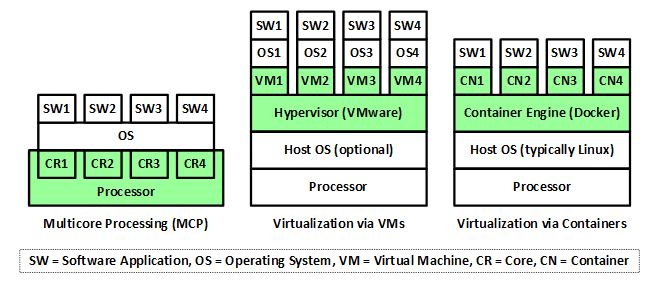
Choosing an operating system is a critical decision for many users, and one great option is an open source operating system. There are several benefits of using an open source operating system, from cost savings to enhanced security. In this article, we’ll explore the many advantages and explain why an open source operating system might be the best choice for you.
Cost-Effective Solution
One of the primary benefits of using an open source operating system is the cost. Open source systems are typically free to use, which can save you a lot of money compared to purchasing a commercial OS. This makes them an attractive option for individuals and organizations looking to cut costs without sacrificing functionality.

Enhanced Security
An open source operating system offers enhanced security features. Since the source code is open to the public, it can be reviewed and audited by anyone. This means that security vulnerabilities are often identified and fixed more quickly than in proprietary systems. The large community of developers continuously works to improve the system, making it more secure over time.
Customization and Flexibility
Another significant advantage of using an open source operating system is the level of customization it offers. You have the freedom to modify the source code to suit your specific needs. This flexibility allows you to tailor the system to your requirements, whether you need it for personal use, business, or development purposes.
Community Support
When you choose an open source operating system, you gain access to a vast community of users and developers. This community is a valuable resource for support, advice, and troubleshooting. Forums, online groups, and documentation are often readily available, making it easier to find solutions to any issues you may encounter.
Transparency
Transparency is a key benefit of an open source operating system. With access to the source code, you can see exactly how the system operates. This level of transparency helps build trust, as users can verify that there are no hidden backdoors or malicious code embedded in the software.
No Vendor Lock-In
Using an open source operating system frees you from vendor lock-in. Proprietary systems often tie you to a specific vendor, limiting your options and potentially leading to higher costs in the long run. With open source, you have the freedom to switch providers or modify the system as needed without being tied to a single vendor.
Innovation and Development
The collaborative nature of open source projects fosters innovation. Developers from around the world contribute to the continuous improvement of the system. This collaborative environment often leads to faster development cycles and the implementation of cutting-edge features and technologies.
Compatibility and Interoperability
Open source operating systems are known for their compatibility and interoperability. They can work well with a variety of hardware and software environments, making them a versatile choice. This broad compatibility ensures that you can integrate the system with existing infrastructure without significant issues.
Performance and Reliability
This reliability is crucial for both personal and business use, ensuring smooth and uninterrupted operation.
Educational Benefits
For students and developers, using an open source system can be highly educational. It provides an opportunity to learn from real-world code and contribute to meaningful projects. This hands-on experience is invaluable for gaining practical skills and knowledge in software development.
Environmentally Friendly
An open source system can also be more environmentally friendly. By extending the life of older hardware through compatibility and efficiency, you can reduce electronic waste. This sustainability aspect is an added benefit for environmentally conscious users.
Scalability
Open source operating systems are often scalable, making them suitable for a wide range of applications.
Freedom and Control
Using an open source system gives you complete freedom and control over your computing environment.
Access to Cutting-Edge Technologies
Open source projects often lead the way in adopting and implementing new technologies. By using an open source system, you can benefit from the latest advancements and innovations in the field of computing.
Conclusion
In conclusion, the benefits of using an open source operating system are numerous. From cost savings and enhanced security to customization and community support, open source systems offer a compelling alternative to proprietary software. By choosing an open-source operating system, you can enjoy a more flexible, transparent, and reliable computing experience.