An operating system (OS) serves as the fundamental software layer that manages the hardware and software resources of a computer. It acts as an intermediary between the user and the hardware, ensuring the system operates smoothly and efficiently. The basic functions of an operating system are crucial for the functioning of computers, enabling users to perform tasks, run applications, and manage data.

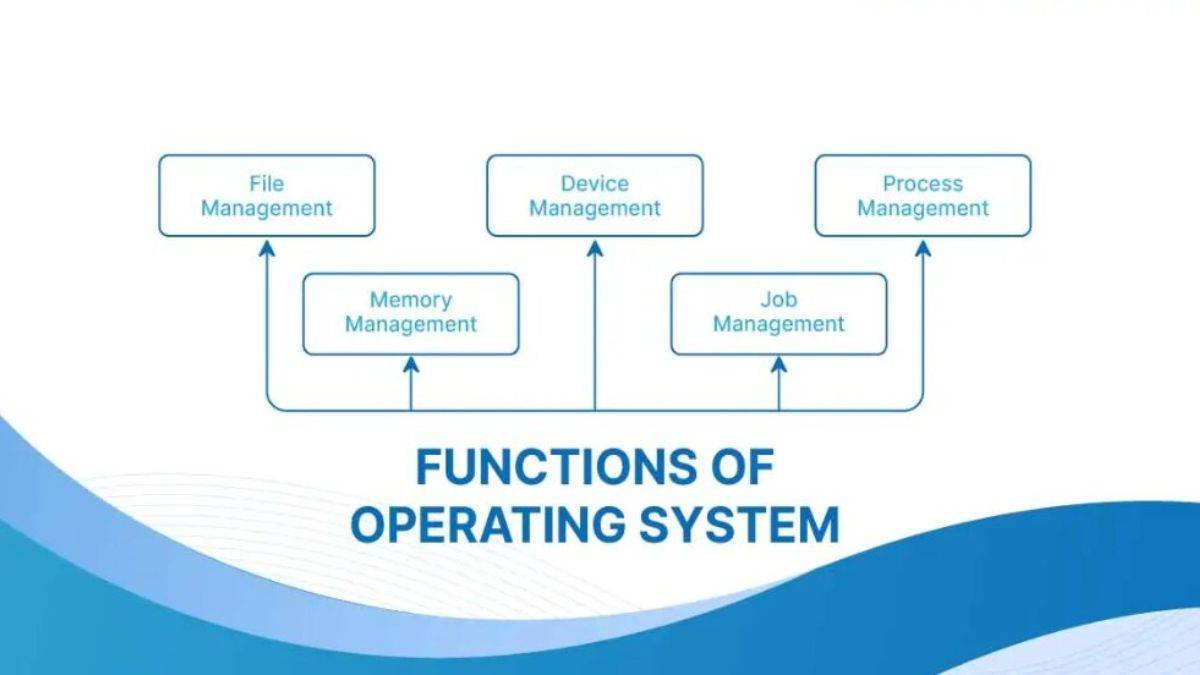
1. Process Management
One of the primary functions of an operating system is process management, which involves handling the creation, scheduling, and termination of processes.
Key Aspects:
- Process Creation and Termination: The OS is responsible for creating processes when a program is launched and terminating them when they complete or are no longer needed.
- CPU Scheduling: The operating system determines the order in which processes access the CPU, optimizing the use of processor time. This includes implementing scheduling algorithms to prioritize processes based on criteria such as urgency and resource requirements.
- Multitasking: Modern operating systems support multitasking, allowing multiple processes to run simultaneously. This is achieved through process switching, where the OS rapidly switches between processes, giving the illusion of concurrent execution.
2. Memory Management
Memory management is another critical function of an operating system, ensuring efficient use of a computer’s memory resources.
Key Aspects:
- Memory Allocation: The OS allocates memory to processes as they run, ensuring each process has the necessary resources. This includes both RAM (Random Access Memory) and virtual memory, which extends physical memory onto disk storage.
- Memory Protection: To prevent processes from interfering with each other, the OS implements memory protection mechanisms. This ensures that one process cannot access the memory space allocated to another, protecting the system from crashes and data corruption.
- Memory Optimization: The OS also optimizes memory usage by reclaiming memory from processes that are no longer active or need less memory. This involves techniques like paging and segmentation, which manage how memory is used and accessed.
3. File System Management
File system management is essential for organizing and storing data on storage devices, such as hard drives, SSDs, and USB drives.
Key Aspects:
- File Organization: The OS organizes data into files and directories, providing a structured way to store and retrieve information. This includes managing file names, file types, and directory structures.
- File Access and Permissions: The operating system controls access to files, ensuring that users and applications have the appropriate permissions. This helps protect data from unauthorized access and modification.
- Storage Management: The OS manages the physical storage on devices, including allocating space for new files, maintaining file integrity, and performing tasks like defragmentation to optimize storage efficiency.
4. Device Management
Device management involves controlling and coordinating hardware components, such as input/output devices, storage devices, and peripherals.
Key Aspects:
- Device Drivers: The OS uses device drivers, which are specialized programs that allow the system to communicate with hardware components. Drivers translate high-level OS commands into low-level instructions that the hardware can execute.
- Device Coordination: The OS manages the interaction between different devices, ensuring that they work together seamlessly. This includes managing data transfers between the CPU, memory, and peripheral devices.
- Resource Allocation: The operating system allocates resources to devices as needed, ensuring efficient use of hardware capabilities. This is particularly important in systems with multiple devices or limited resources.
5. Security and Access Control
Security and access control are vital functions of an operating system, protecting the system and data from unauthorized access and potential threats.
Key Aspects:
- User Authentication: The OS verifies the identity of users through login credentials, such as usernames and passwords, ensuring that only authorized users can access the system.
- Access Control: The OS enforces access control policies, determining what actions users can perform on files, directories, and other resources. This helps prevent unauthorized access and modification of sensitive data.
- Security Features: Modern operating systems include a range of security features, such as encryption, firewalls, and antivirus integration, to protect against malware and other security threats.
Conclusion
The basic functions of an operating system are foundational to the operation of any computer system. By managing processes, memory, files, devices, and security, the OS ensures that users can interact with the system efficiently and securely. As technology continues to advance, operating systems evolve to incorporate new features and improvements, maintaining their critical role in computing.