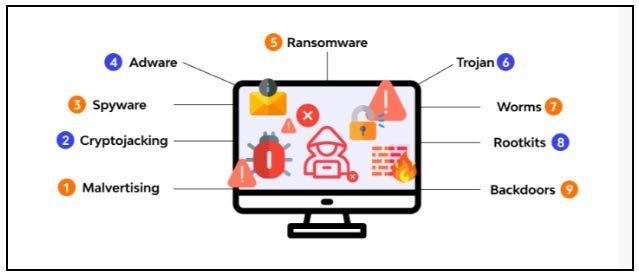
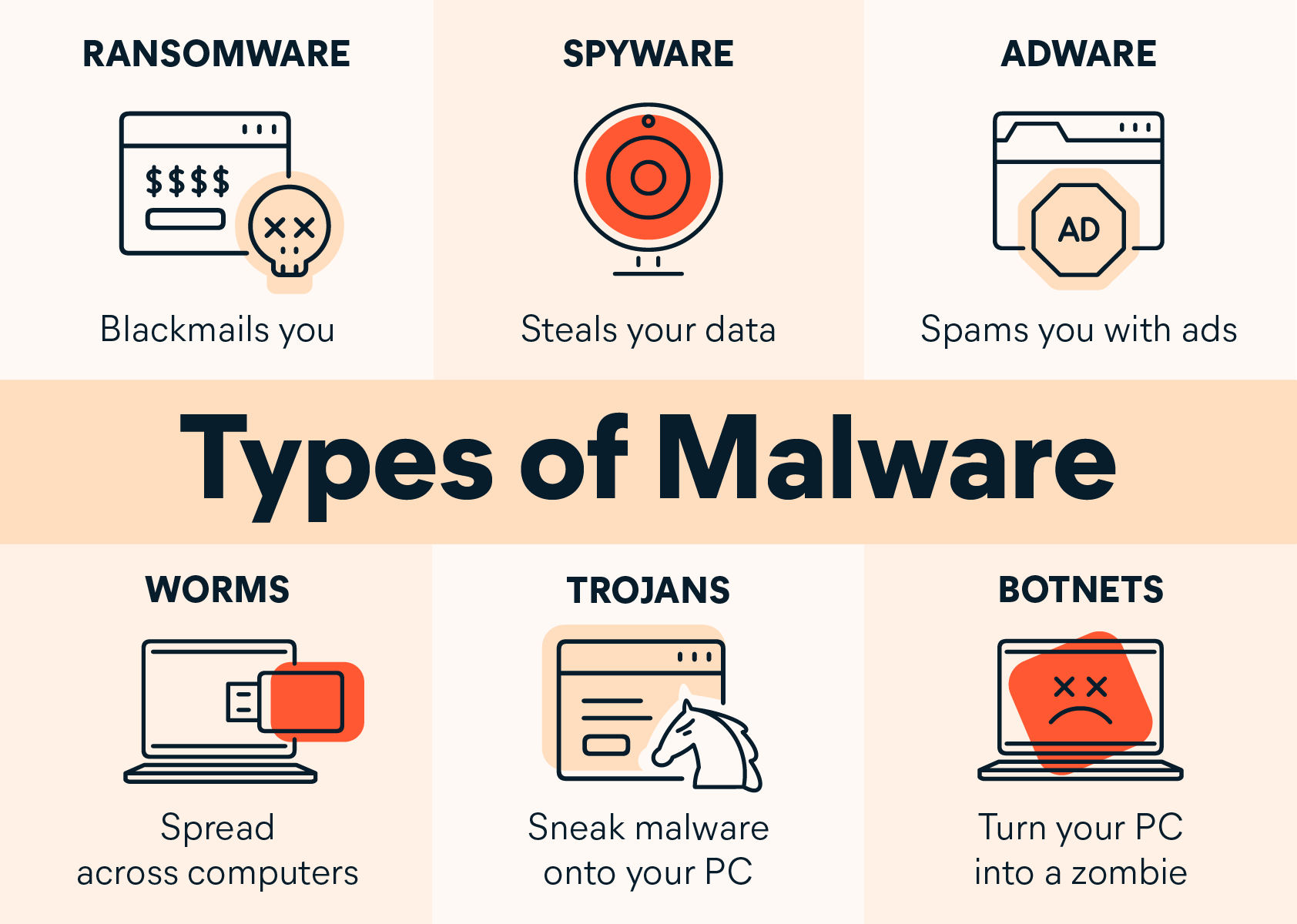
In the ever-evolving landscape of cybersecurity, implementing best practices is essential for protecting digital assets, maintaining system integrity, and ensuring data confidentiality. These practices help mitigate risks, prevent breaches, and safeguard against a wide range of threats. This article outlines key best practices for security, focusing on both personal and organizational approaches.

1. Implement Strong Password Policies
Overview: Passwords are a fundamental line of defense against unauthorized access. Strong password policies help ensure that passwords are difficult for attackers to guess or crack.
Best Practices:
- Use Complex Passwords: Create passwords that include a mix of uppercase letters, lowercase letters, numbers, and special characters.
- Avoid Common Passwords: Steer clear of easily guessable passwords, such as “password123” or “admin.”
- Implement Password Length Requirements: Enforce a minimum length for passwords, typically at least 8-12 characters.
- Encourage Password Changes: Regularly update passwords and avoid reusing old passwords across different accounts.
- Use Password Managers: Employ password managers to securely store and generate complex passwords.
2. Enable Multi-Factor Authentication (MFA)
Overview: Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to access accounts or systems.
Best Practices:
- Use MFA for Sensitive Accounts: Enable MFA for critical accounts, such as email, financial accounts, and administrative access.
- Select Strong Authentication Methods: Choose reliable authentication methods, such as SMS codes, authentication apps, or hardware tokens.
- Educate Users on MFA: Ensure that users understand the importance of MFA and how to use it effectively.
3. Regularly Update and Patch Systems
Overview: Keeping software, operating systems, and applications up to date is crucial for protecting against known vulnerabilities and security flaws.
Best Practices:
- Establish a Regular Update Schedule: Regularly check for and apply updates and patches to all software and systems.
- Automate Updates Where Possible: Use automated tools to manage updates and ensure timely application.
- Test Updates Before Deployment: Test updates in a controlled environment to identify potential issues before applying them to production systems.
4. Implement Firewalls and Antivirus Software
Overview: Firewalls and antivirus software are essential for defending against malicious attacks and unauthorized access.
Best Practices:
- Deploy Firewalls: Use both hardware and software firewalls to monitor and control incoming and outgoing network traffic.
- Install Antivirus Software: Employ reputable antivirus software to detect and remove malware and other threats.
- Regularly Update Security Software: Keep antivirus and firewall software updated to protect against the latest threats.
5. Encrypt Sensitive Data
Overview: Encryption protects sensitive data by converting it into an unreadable format that can only be decrypted with the correct key or password.
Best Practices:
- Encrypt Data at Rest and in Transit: Use encryption to protect data stored on devices and transmitted over networks.
- Use Strong Encryption Standards: Apply well-established encryption algorithms, such as AES-256, for securing data.
- Manage Encryption Keys Securely: Protect and manage encryption keys to prevent unauthorized access.
6. Backup Data Regularly
Overview: Regular data backups ensure that important information can be recovered in case of data loss, corruption, or ransomware attacks.
Best Practices:
- Create Automated Backups: Set up automated backup processes to regularly back up critical data.
- Store Backups Securely: Keep backups in secure locations, such as offsite storage or cloud services, to protect against physical and cyber threats.
- Test Backup Restoration: Regularly test backup restoration processes to ensure data can be recovered successfully.
7. Educate and Train Users
Overview: User awareness and training are crucial for preventing security breaches and ensuring that employees follow best practices.
Best Practices:
- Conduct Regular Training: Provide cybersecurity training to employees on topics such as phishing, password management, and safe browsing practices.
- Simulate Phishing Attacks: Use simulated phishing exercises to test user awareness and identify areas for improvement.
- Promote a Security Culture: Encourage a culture of security awareness and responsibility within the organization.
8. Monitor and Respond to Security Incidents
Overview: Effective monitoring and response strategies help detect and address security incidents promptly.
Best Practices:
- Implement Security Monitoring Tools: Use monitoring tools to detect suspicious activities, unauthorized access, and potential breaches.
- Develop an Incident Response Plan: Create and maintain an incident response plan to guide actions during security incidents.
- Conduct Regular Security Audits: Perform regular security audits and assessments to identify vulnerabilities and improve defenses.
9. Limit Access and Permissions
Overview: Limiting access and permissions helps reduce the risk of unauthorized access and potential damage.
Best Practices:
- Apply the Principle of Least Privilege: Grant users the minimum level of access necessary for their roles and responsibilities.
- Review Access Rights Regularly: Periodically review and adjust access rights to reflect changes in roles or organizational structure.
- Use Role-Based Access Control: Implement role-based access control (RBAC) to manage permissions based on user roles and responsibilities.
10. Secure Physical Access
Overview: Physical security is an often-overlooked aspect of cybersecurity that involves protecting hardware and infrastructure.
Best Practices:
- Restrict Access to Sensitive Areas: Limit physical access to server rooms, data centers, and other critical infrastructure.
- Use Physical Locks and Security Measures: Employ locks, access cards, and surveillance systems to secure physical locations.
- Monitor and Record Access: Keep records of who accesses sensitive areas and regularly review access logs.
11. Stay Informed About Emerging Threats
Overview: Keeping abreast of the latest cybersecurity threats and trends helps adapt defenses to evolving risks.
Best Practices:
- Follow Cybersecurity News: Stay updated on the latest threats, vulnerabilities, and security practices through news sources and industry publications.
- Participate in Security Communities: Engage with cybersecurity communities, forums, and professional networks to share knowledge and insights.
- Attend Security Conferences: Attend conferences and training sessions to learn about new technologies and threat landscapes.
12. Conclusion
Implementing best practices for security is essential for protecting digital assets, ensuring system stability, and mitigating risks. By adopting these practices, including strong password policies, multi-factor authentication, regular updates, and user education, organizations and individuals can enhance their cybersecurity posture and safeguard against potential threats.