In today’s digital landscape, cybersecurity threats are increasingly sophisticated and pervasive. Among these threats, malware, viruses, and ransomware are some of the most common and damaging. Understanding these threats, their characteristics, and how they operate is crucial for protecting systems and data from malicious attacks. This article provides a comprehensive overview of malware, viruses, and ransomware, highlighting their differences, how they spread, and strategies for mitigating their impact.
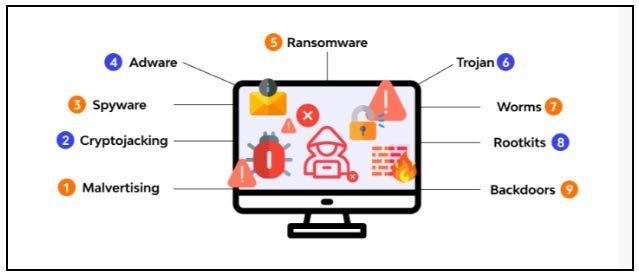
1. Malware
Overview:
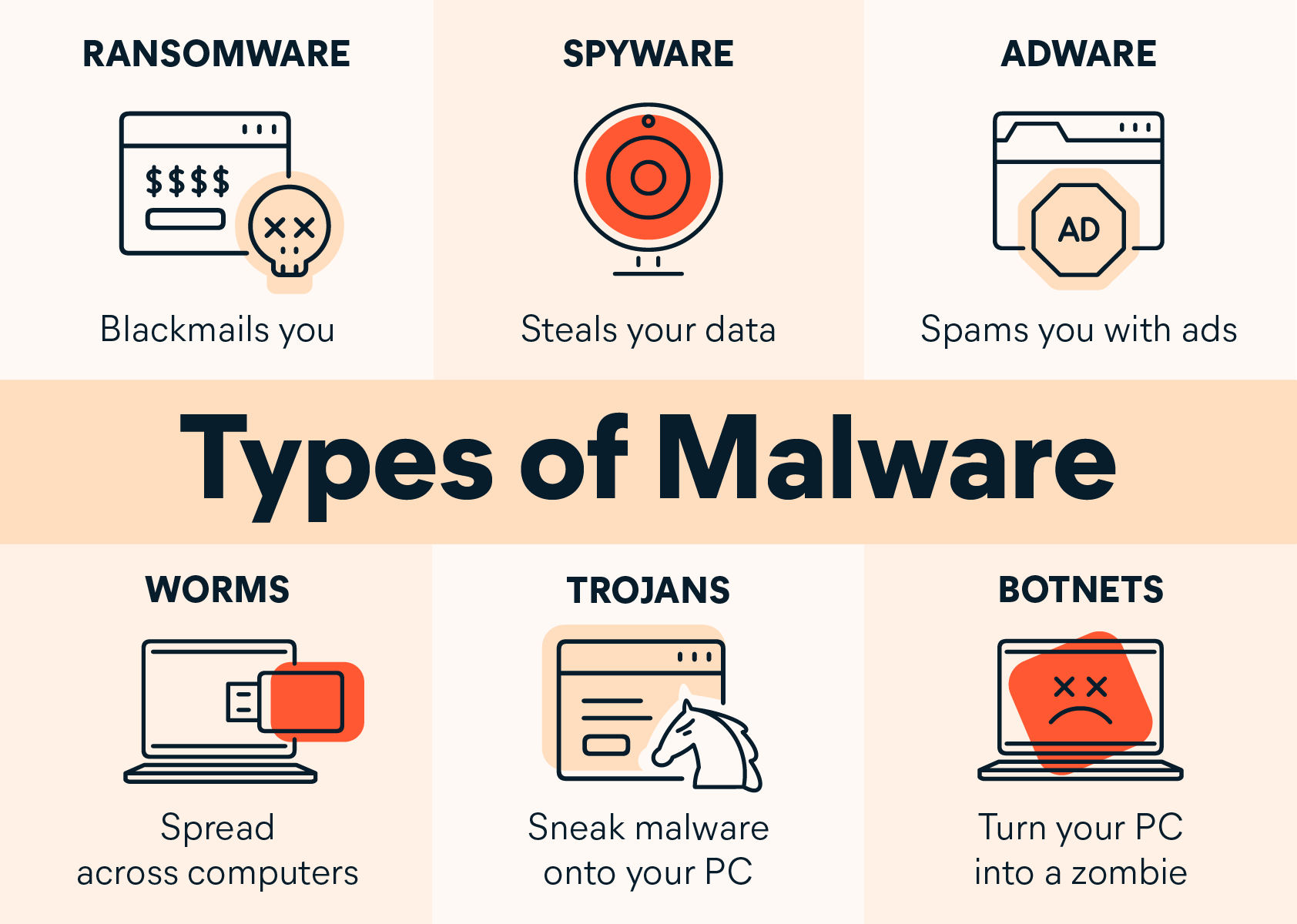
Malware, short for “malicious software,” is a broad term that encompasses various types of harmful software designed to damage, disrupt, or gain unauthorized access to systems and data. Malware includes viruses, worms, trojans, ransomware, spyware, and adware.
Types of Malware:
- Viruses:
- Description: A type of malware that attaches itself to legitimate files or programs and spreads to other files and systems. It can corrupt, delete, or steal data.
- Propagation: Typically spreads through infected email attachments, compromised websites, or shared files.
- Impact: Can cause system crashes, data loss, and performance issues.
- Worms:
- Description: Malware that replicates and spreads independently across networks without needing to attach to files. Worms exploit vulnerabilities in network protocols or software.
- Propagation: Spreads through network connections, email, or malicious downloads.
- Impact: Can cause widespread network congestion, system slowdowns, and data breaches.
- Trojans:
- Description: Malware disguised as legitimate software or files to trick users into installing it. Once installed, it can perform various malicious activities.
- Propagation: Often delivered through phishing emails or fake software downloads.
- Impact: Can provide unauthorized access to systems, steal data, or facilitate further attacks.
- Spyware:
- Description: Malware designed to secretly collect and transmit user data, such as browsing habits, keystrokes, or personal information.
- Propagation: Installed through deceptive software or infected websites.
- Impact: Compromises user privacy and can lead to identity theft.
- Adware:
- Description: Software that displays unwanted ads or pop-ups, often bundled with legitimate programs. While not always harmful, it can be intrusive and affect system performance.
- Propagation: Typically bundled with free software or downloaded from untrusted sources.
- Impact: Can degrade user experience and system performance.
Best Practices for Protecting Against Malware:
- Use Reliable Security Software: Install and maintain up-to-date antivirus and anti-malware programs.
- Keep Software Updated: Regularly update operating systems and applications to patch vulnerabilities.
- Avoid Suspicious Links: Be cautious with email attachments, links, and downloads from unknown sources.
- Backup Data: Regularly backup important data to prevent loss in case of an infection.
2. Viruses
Overview:
A virus is a specific type of malware that attaches itself to legitimate files or programs and spreads to other files or systems when the infected file is executed. Viruses can cause a range of issues, from minor disruptions to severe data loss.
Characteristics of Viruses:
- Replication: Viruses replicate by inserting copies of themselves into other files or programs.
- Activation: A virus activates when the infected file or program is executed, triggering the malicious code.
- Payload: The payload is the part of the virus responsible for causing harm, such as deleting files, corrupting data, or stealing information.
Types of Viruses:
- File Infector Viruses: Attach to executable files and spread when the infected file is run. Examples include CIH (Chernobyl) and Sasser.
- Macro Viruses: Infect documents with macros, such as Microsoft Office files, and spread through infected documents. Examples include Melissa and Concept.
- Polymorphic Viruses: Change their code to avoid detection by antivirus software. Examples include Storm Worm and Marburg.
- Metamorphic Viruses: Rewrite their own code each time they infect a new file to evade detection. Examples include ZMist and Simile.
Best Practices for Protecting Against Viruses:
- Use Antivirus Software: Regularly scan files and programs with updated antivirus tools.
- Be Cautious with Email: Avoid opening email attachments or links from unknown senders.
- Enable File Extensions: View file extensions to identify potentially suspicious files.
- Practice Safe Browsing: Avoid visiting untrusted websites or downloading files from unreliable sources.
3. Ransomware
Overview:
Ransomware is a type of malware that encrypts a victim’s files or locks their system, rendering it unusable until a ransom is paid to the attacker. Ransomware attacks can be devastating, leading to significant data loss and financial damage.
How Ransomware Works:
- Infection: Ransomware typically enters a system through phishing emails, malicious attachments, or exploit kits that target software vulnerabilities.
- Encryption: Once installed, ransomware encrypts files on the victim’s system using strong encryption algorithms, making them inaccessible without the decryption key.
- Ransom Demand: The attacker demands a ransom, usually in cryptocurrency, for the decryption key. Instructions for payment are often provided through a ransom note displayed on the victim’s screen.
- Decryption: If the ransom is paid, the attacker may provide the decryption key to restore access to the encrypted files. However, there is no guarantee that the attacker will honor the demand.
Notable Ransomware Examples:
- WannaCry: Spread rapidly in 2017, exploiting a vulnerability in Windows systems and affecting organizations worldwide.
- NotPetya: Targeted businesses in 2017 with destructive payloads, causing widespread disruption.
- Ryuk: Known for targeting high-profile organizations and demanding large ransoms.
Best Practices for Protecting Against Ransomware:
- Regular Backups: Regularly backup important files and store backups offline or in a secure cloud service.
- Update Systems: Apply security patches and updates to protect against known vulnerabilities.
- Educate Users: Train users to recognize phishing attempts and avoid suspicious links or attachments.
- Use Security Software: Employ comprehensive security solutions that include ransomware protection and real-time monitoring.
Conclusion
Malware, viruses, and ransomware pose significant threats to systems and data, each with distinct characteristics and methods of attack. Understanding these threats and implementing robust security measures are essential for protecting against malicious activities. By adopting best practices for malware protection, staying vigilant against viruses, and preparing for ransomware attacks, individuals and organizations can enhance their cybersecurity defenses and safeguard their digital assets.